The following command line commands are in hot demand right now on the market. Plus, one of them, ncat, is often featured in movies as a hacker tool. Here is Trinity using it in the Matrix:
Table of Contents
WHOIS
sudo apt install whois
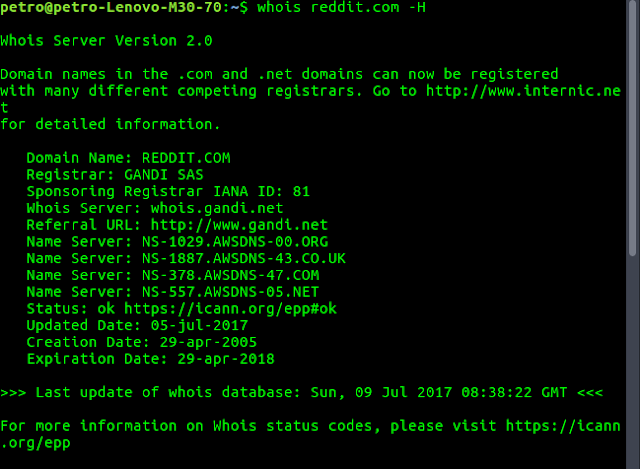
whois reddit.comA helpful flags is -H, which removes all the legalese:
whois reddit.com -HWHois in action:

Ping
This basic command is a helpful diagnostic tool for network problems. It also returns the IP address of a domain. I also like to let it in the background if an Internet connection keeps dropping, sometimes it keeps it alive. Also, if you can ping an IP address but not a domain name, you have a DNS problem.ping reddit.com
Traceroute
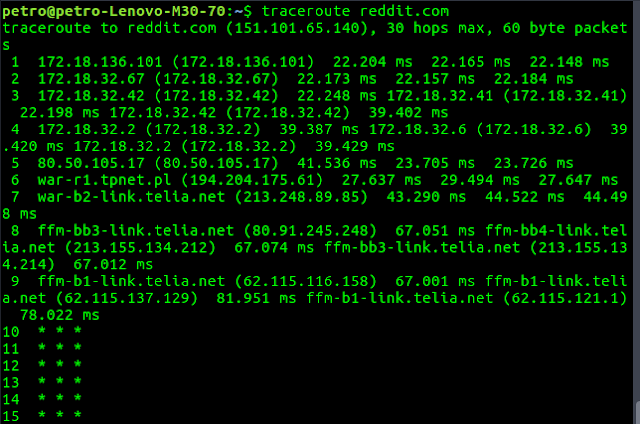
While ping displays information for a entire connection, traceroute does for every step along the way.sudo apt install traceroute
traceroute reddit.com

Transmission Control Protocol Dump
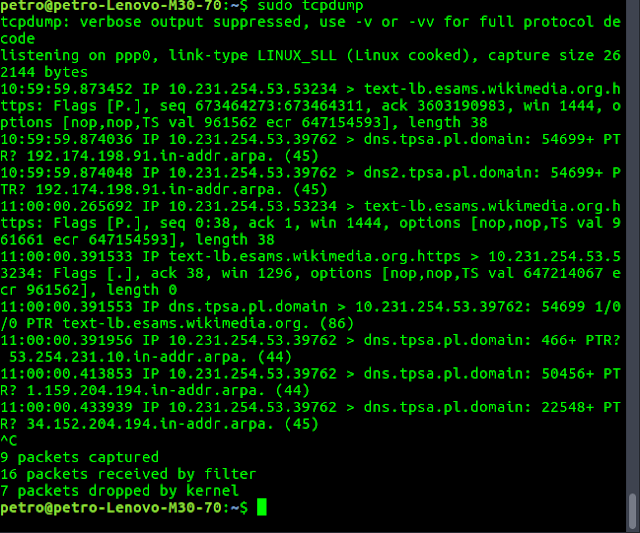
Transmission Control Protocol (TCP) dump displays TCP and other packets being transmitted over the network. You need superuser (sudo) permissions to run it:sudo tcpdumpIn action:

Network Mapper
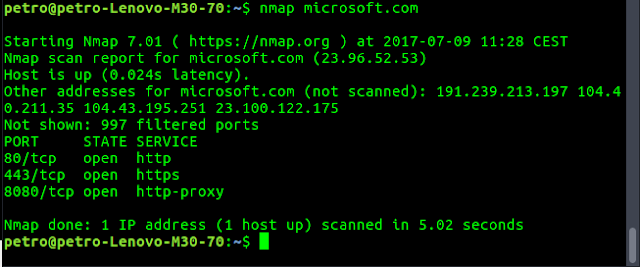
Network Mapper (nmap) uses packets to build a map of a network. It was featured in the sequel to the best movie ever, the Matrix (video clip below):sudo apt install nmap
nmap microsoft.com

Netcat
Netcat uses TCP or UDP to form and read network connections.ncat -C scanme.nmap.org 80To give it a whirl, after you hit enter, input:
ncat -C scanme.nmap.org 80Then hit enter twice (for real, twice, or it won't work). When you get it to work, it will look like this:
Simple Network Management Protocol
snmptranslate .1.3.6.1.2.1.1.3.0 Net-SNMP is a suite of applications used to monitor network health. To install:sudo apt install snmpFor example:
snmptranslate .1.3.6.1.2.1.1.3.0Outputs:
OpenSSL
OpenSSL (SSL = Secure Sockets Layer) is a technology that helps secure computer network communications against eavesdropping. We can start out with secret key encryption algorithms. For example:touch.txtPress Enter.
echo "testing" > number.txtPress Enter.
openssl enc -base64 -in number.txtWe get:



Comments
Post a Comment
Comments are welcome and a good way to garner free publicity for your website or venture.